Google Cloud is a secure cloud platform that provides the foundation for building reliable, scalable, and secure applications. Security is a top priority for Google Cloud, and they work hard to ensure that the platform is as secure as possible. Comprehensive security features include authentication and authorization, data encryption, and intrusion detection. With Google Cloud, you can be confident that your data is safe and protected at all times.
A secure cloud application is one that is designed with security in mind. Security is critical for (m)any application, but it is especially important for cloud applications, which are often accessed by a large number of users. A secure cloud application is designed to protect against unauthorized access, data loss, and other threats.
Threats to Cloud Computing
The Cloud Security Alliance (CSA) is a nonprofit organization that is dedicated to helping organizations adopt cloud computing securely. The CSA identified the top nine key threats that are associated with cloud computing:
- Data Loss: Data can be lost due to hardware or software failures, human error, or malicious attacks.
- Insecure APIs: The reliance on weak APIs exposes organizations to a wide range of security risks, particularly in the area of confidentiality, integrity, availability, and accountability.
- Malicious Insiders: Malicious insiders, such as disgruntled employees, can pose a serious threat to the security of cloud computing systems.
- Account Hijacking: Account hijacking is a type of attack in which an attacker gains unauthorized access to a user’s account. This can be done through, fraud, phishing, and exploitation of vulnerabilities in software and cloud platforms.
- Data Leakage: Data leakage can occur when data is transferred outside of the organization without proper security controls in place. This can happen through email, USB drives, and other removable media.
- Shared Technology Issues: Shared technology concerns, such as shared hosting and virtualization, can put organizations using cloud services that were not built to provide secure isolation at risk.
- Denial Of Service (DoS): A denial of service attack can prevent users from accessing your applications or data. This can happen by flooding your systems with requests or traffic so that they are unable to respond to legitimate requests.
- Insufficient Due Diligence: Organizations need to carefully assess the security risks of any cloud service before adoption. This includes understanding how the service works, what data will be stored in the cloud, and who will have access to it.
- Cloud Abuse: The misuse of cloud services, such as using a storage service to host illegal content, can put your organization at risk. Other abuse includes the use of cloud services to launch attacks DDOS attacks on other organizations.
In order to protect against these threats, it is important to design your applications with security in mind. Some of the most important considerations include using the proper authentication methods, granting the least privileged access, and using appropriate security measures.
How Google Cloud ensures security
Google Cloud Platform has a number of comprehensive security features that help to protect your data and applications. Security is built-in from the start, and it is never bolted on. Security on cloud platforms is the responsibility of both the customer and the provider. Google Cloud Platform has a model that shares responsibility with the customer who uses their platform.
Shared Responsibility Model for Google Cloud Platform
The shared responsibility model is a security approach that requires both the customer and the service provider to take measures to protect data and systems. This means that, while Google Cloud is responsible for securing the infrastructure, you are responsible for securing your data and applications.
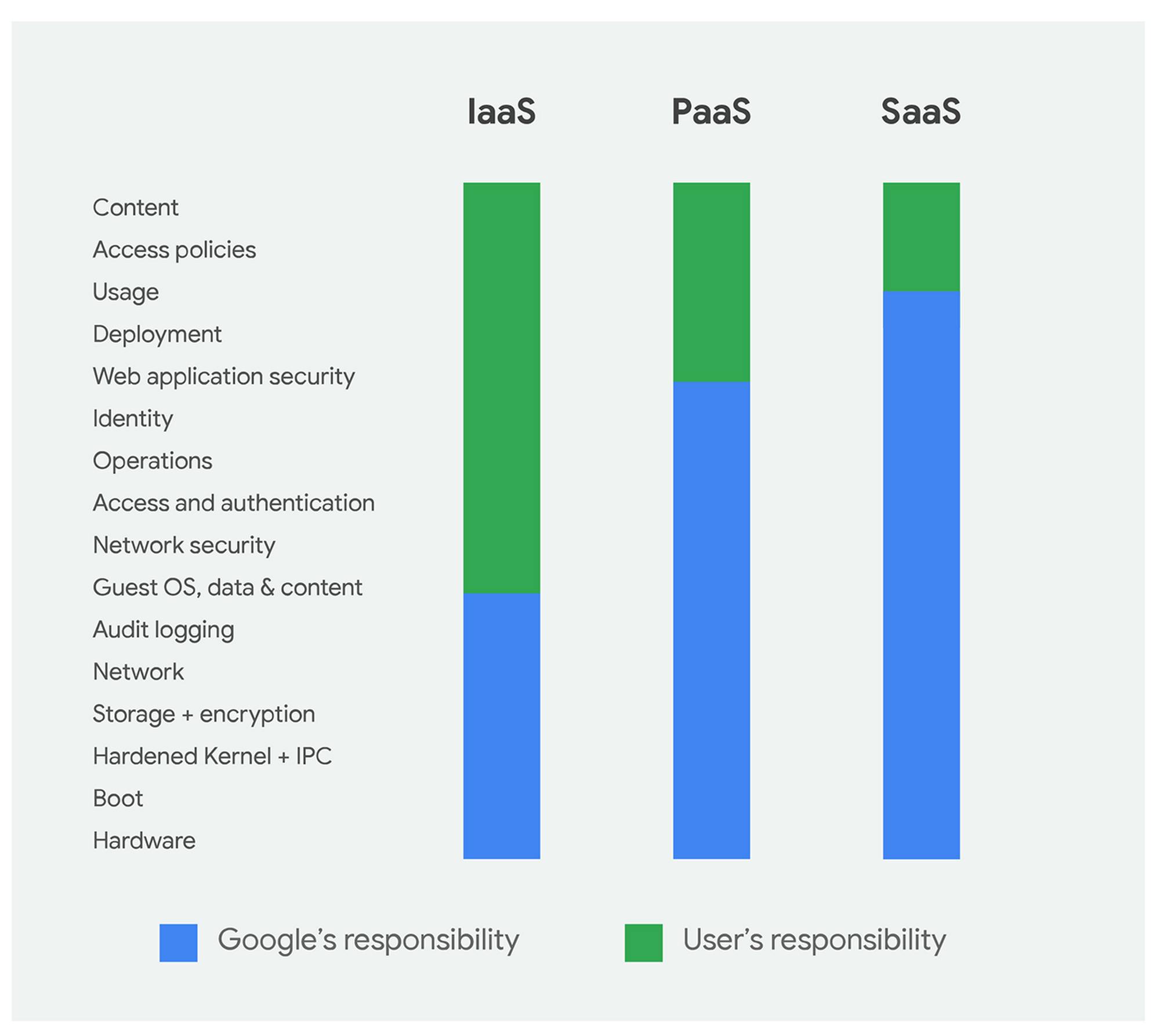 Source: Google
Source: Google
The Shared Responsibility Model can be summarised as:
- The customer is in charge of defining data and applications' access restrictions on Google Cloud. In order to securely use the Google Cloud Platform, you need to take measures to protect your data and applications. This includes using the proper authentication methods, granting the least privileged access, and using appropriate security measures.
- The service provider, Google is responsible for the underlying infrastructure. How Does Google Secure Its Infrastructure? Google has a number.
- What is made available for you to configure is your responsibility, for example, which regions to store your data in, what user permissions to set up, and so on. If don't have access to change, modify or delete a resource, then that's probably because it falls under Google Cloud's remit to manage.
In order to help you meet your security obligations, Google Cloud provides a number of tools and services, including:
- Identity and Access Management (IAM): IAM enables you to control who has access to your Google Cloud resources. You can use IAM to create users, groups, and roles, as well as to set permissions for what each user, group, or role can do within your account.
- Secure Sockets Layer (SSL) Certificates: SSL certificates are used to encrypt traffic between your users and your website. Google Cloud provides free SSL certificates for all websites hosted on Google App Engine, Cloud Run, Firebase and GCS.
- Security Command Center: The Security Command Center provides a central location for you to view and manage security risks across your Google Cloud resources. The Security Command Center enables you to detect, investigate, and respond to security threats.
- Cloud Audit Logs: Cloud Audit Logs provide a record of actions taken by users, groups, and services on your Google Cloud resources. These logs can be used to track changes made to your resources and to help you troubleshoot issues.
- Cloud Data Loss Prevention: Cloud Data Loss Prevention (DLP) is a service that helps you protect your sensitive data. Sensitive data includes Personally Identifiable Information (PII), and Personally Protected Health Information (PHI). DLP can scan your data for over 80 types of sensitive information, such as credit card numbers, date of birth, addresses and social security numbers.
- Secure Application Development: Google Cloud Platform provides a number of tools and services to help you secure your applications, including Web Security Scanner, which helps you find vulnerabilities in your App Engine, Google Kubernetes Engine (GKE), and Compute Engine web applications.
- Advisory Notifications: Advisory Notifications provide well-targeted, timely, and compliant notifications about security and privacy incidents in the Google Cloud console so you can investigate the situation, respond, and get assistance.
In order to ensure that your data is secure on the Google Cloud Platform. Google provides a comprehensive set of security features and a commitment to keeping your data safe, they take the following measures:
- 24/7 physical security at global data centres: Data centres are the backbone of any cloud provider, and security is of the utmost importance. Google’s data centres are some of the most secure in the world, with 24/7 physical security, state-of-the-art surveillance systems, and strict access controls.
- Regular third-party audits: In order to ensure that our security measures meet the highest standards, Google regularly undergoes independent third-party audits. These audits cover a wide range of security topics, including physical security, network security, and information security. Google Cloud is committed to providing a secure cloud platform for customers.
- Your data is always encrypted: While at rest, in memory or in transit within Google Cloud Platform products so that it is protected from unauthorized access.
- Infrastructure Security: Google Cloud Platform uses a number of physical and logical security measures to protect your data, including firewalls, intrusion detection and prevention systems, and physical security measures.
These are just some of the ways that Google Cloud Platform ensures security. Secure cloud applications are critical for businesses today. With so much data being stored in the cloud, it's essential that this data is protected from unauthorized access. When you use Google Cloud Platform, you can be confident that your data and applications are secure. I hope you enjoyed this post and please feel free to leave any comments or questions below. Thanks for reading !